In the rapidly evolving landscape of cybersecurity, outdated security protocols can pose significant risks to your digital assets. These old protocols may contain vulnerabilities that could be exploited by malicious actors, potentially leading to data breaches, unauthorized access, and other security breaches. Recognizing and addressing these issues promptly is crucial to maintaining the integrity and security of your digital infrastructure.

Why is it important for you to fix this issue? Failure to address these issues promptly could leave your systems vulnerable to cyber attacks, resulting in potential financial losses, reputational damage, and legal repercussions. By taking proactive steps to update and strengthen your security protocols, you demonstrate a commitment to protecting your organization and its stakeholders from potential threats.
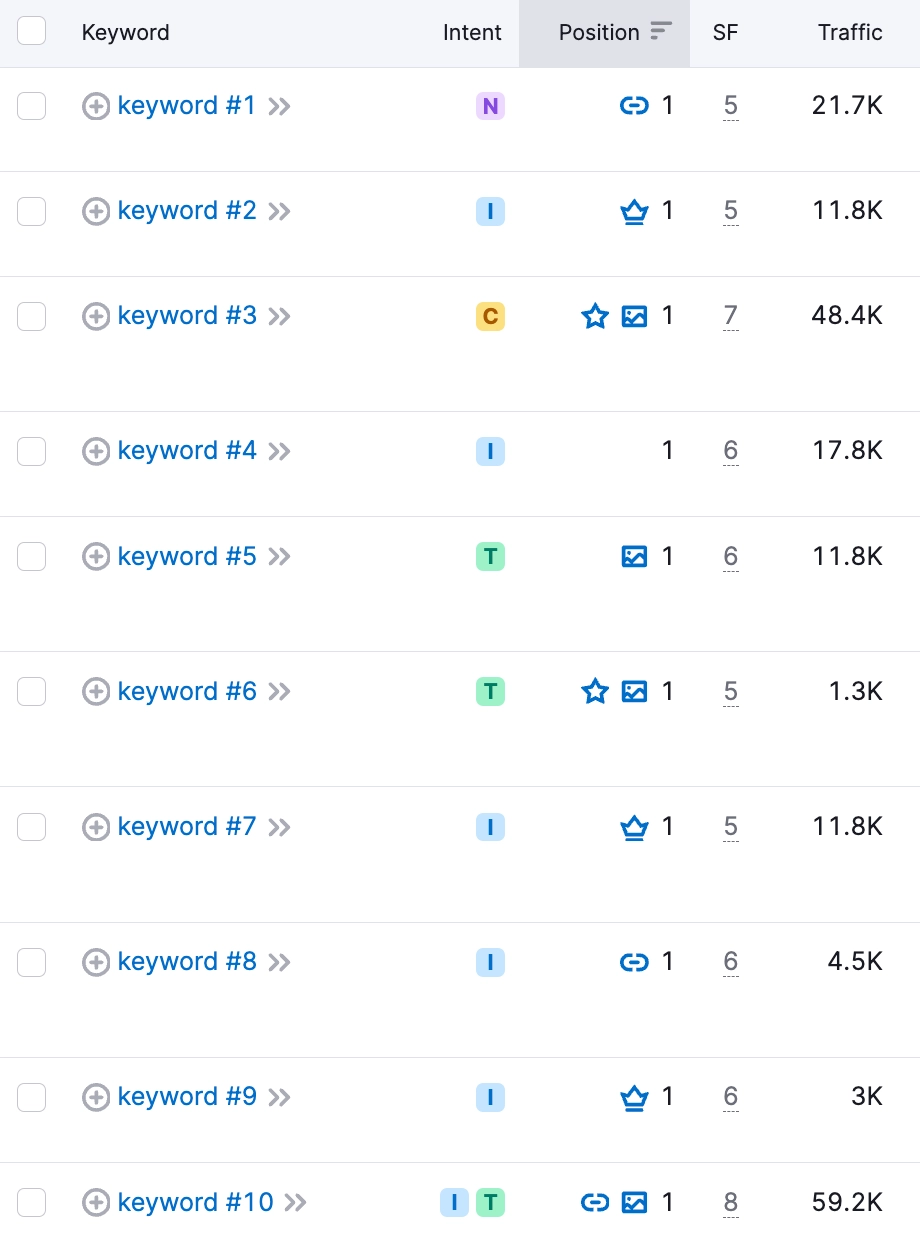
How to Fix “Issues With Old Security Protocol” Detected by a Semrush Audit
Step 1: Identify the Old Security Protocol
- Begin by identifying which specific security protocol is flagged as outdated by the Semrush Audit. Common examples include SSL 2.0, SSL 3.0, and TLS 1.0.
- Use the information provided in the Semrush report to pinpoint the exact areas of your website where the old security protocol is being used.
Step 2: Update Server Configuration
- Log in to your web server’s control panel or access the server via SSH.
- Update the server configuration to disable the use of the outdated security protocol.
- Consult your server documentation or contact your hosting provider for guidance on how to make these changes safely.
Step 3: Update SSL/TLS Certificates
- Check the validity and expiration dates of your SSL/TLS certificates.
- If necessary, renew your certificates to ensure they are up-to-date and compliant with modern security standards.
- Consider upgrading to a higher level of encryption (e.g., SHA-2) for improved security.
Step 4: Update Web Server Software
- Ensure that your web server software (e.g., Apache, Nginx) is running the latest version.
- Update the server software to ensure compatibility with modern encryption protocols and security standards.
- Follow the documentation provided by your server software vendor to perform the update safely.
Step 5: Test Website Security
- After implementing the necessary changes, conduct thorough testing to verify that the old security protocol has been successfully disabled.
- Utilize online tools or security scanners to perform vulnerability assessments and confirm that your website is now using secure encryption protocols.
- Monitor your website regularly for any potential security issues and promptly address any new vulnerabilities that may arise.
Step 6: Update the Content Management System (CMS) and Plugins
- If your website is built on a CMS platform (e.g., WordPress, Joomla), ensure that both the core CMS and any installed plugins or extensions are kept up-to-date.
- Regularly check for updates and security patches released by the CMS developers and plugin authors.
- Update your CMS and plugins promptly to mitigate potential security risks associated with outdated software.
Step 7: Implement Best Security Practices
- In addition to updating encryption protocols, implement best practices for website security, such as using strong, unique passwords, enabling two-factor authentication, and regularly backing up your website data.
- Stay informed about emerging security threats and industry best practices to proactively protect your website against new vulnerabilities.
By diligently following these steps and placing a paramount emphasis on fortifying the security of your digital infrastructure, you can adeptly tackle the identified “Issues With Old Security Protocol” flagged by the Semrush audit, thereby enhancing the resilience of your organization against potential security vulnerabilities. However, should these measures not yield the desired results, it may be beneficial to seek the guidance of our SEO specialist. Their expertise can offer invaluable insights and tailored strategies to navigate through any lingering challenges, ensuring a robust and secure digital environment for your organization.